Cybersecurity 206: Content Delivery Networks CDNs as Information Shield or Adversarial Propaganda Dispenser
Why did we start using Content Delivery Networks CDNs and how are CDNs being exploited by our enemies?
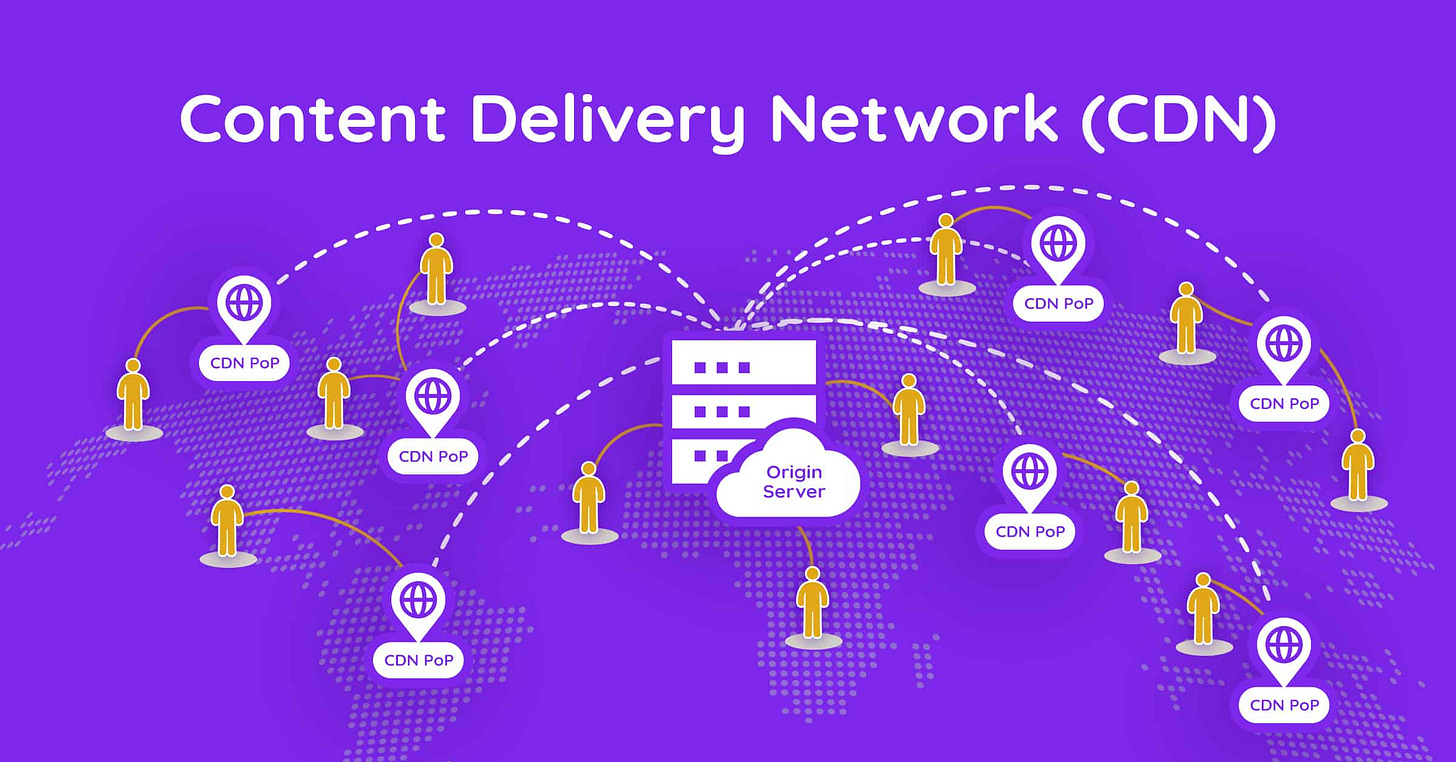
Content Delivery Networks (CDNs) are supposed to enable rapid information caching and downloads to local users. In otherwords, you have a CDN for part of the internet, that is supposed to be a carbon-copy per say of the original website. However, any information technology IT expert knows that geolocation tagging has been used for decades now to adjust content specific to a given location. Therefore, the CDNs that are in given regions (think each state if you are in United States of America or city for that matter).
The original uses were to provide a local data repository, then delivery this quicker to the consumer of information. Then geolocation content updating became the norm. Then with the use of Artificial Intelligence AI, the CDNs were further upgraded to link the content delivered to you when you search on a search engine to be relevant and maximize consumer to spend conversion.
People have detected the AI and CDNs by conversations talking about a given product (e.g. barbque pit) or football team and then having the content displayed to them for the given football team on an advertisement. Majority of technical and even some non-technical people have picked on this AI CDN interaction for marketing and messaging (marcom in industry lingo terms). However, things just got super weird with this AI CDN when you add neurotechnology to it and non-invasively dosed brain-machine-interfaces niBMIs. How so?
Now, with non-invasively dosed brain-machine-interfaces niBMIs the machine links your thoughts to the CDN, so not only what you speak aloud, or type and search for, but now what you are thinking real-time.
Therefore, the information you are provided, is limited to your pre-existing knowledge. If you are unaware of a topic, you will literally never be served the topic or information by a search engine that is not free of “cognitive blinders” per say. This is how the entire field of “neurotechnology” is being hidden from an average person that is not neuroaware. Further, the use of misinformation can be delivered through a CDN to mislead anyone looking into neurotechnology. This has been the historical use case of neurotechnology, to blind those from learning about it by intelligence communities. However, now with ChinaCCP PLA Xi’s Magic Weapon, neurostrike, is taking advantage of this critical vulnerability, think of it as an Achilles’ Heel in the NATO IC or 5 Eyes National Security Alliance. Make no mistake, our own systems in the West are being used against us, but covertly and secretly through ChinaCCP PLA Xi’s Magic Weapon, such that technically it is our own systems being used against us, but digging deeper it is the false-positing by ChinaCCP PLA Xi’s Magic Weapon defeating our 5 Eyes National Security systems by using the system on itself. An analogy is the East is making the West turn in on itself through the cyberhacking and neurohacking of the West’s 5 Eyes systems, inclusive of neurotechnology.
So, how to avoid adversarial CDNs? Make sure your electronic hardware is not from ChinaCCP coalition, such that the chipsets in it are neurotechnology hardwired pipelines to ChinaCCP and further, make sure that you’re not consuming any ChinaCCP apps, specifically Tik Tok is their nation’s preferred propoganda misinformation spreader through use of neurotechnology, cyber and neuro attack vectors. [1,2]
ChinaCCP PLA using CDNs and DNS cybersecurity hacks to digitally enable their historical warfare tactic of surround and isolate a given force. [0]
[0] https://www.usni.org/magazines/proceedings/2021/march/chinas-three-information-warfares
[1] https://www.washingtontimes.com/news/2023/sep/5/time-to-protect-chinese-americans-targeted-by-ccp-/
[2] https://www.washingtontimes.com/news/2023/dec/20/inside-ring-chinese-brain-warfare-includes-sleep-w/


If all internet users' thoughts are recorded in real-time how can this immense amount of data be stored, processed and acted upon? And what sources power these quantum computers?