Cybersecurity 213: How to Harden Your Network & Hardware against Neurohacker Electronic Hardware Penetration Points
Based upon our team's reverse engineering of a failed neuroweapon persistent state attack by ChinaCCP Coalition, here are the penetration points to harden your networks and computers against.
Based upon work completed from 2022 2nd QTR through 2024 1st QTR, here are “hardware” penetration points for neurohackers to attack your government, corporation, organization or home computer systems.
Laptops with chipsets in them that enable neurotechnology or wireless
IoT devices with chipsets in them that enable neurotechnology or wireless
Televisions with chipsets in them that enable neurotechnology or wireless
Monitors with chipsets in them that enable neurotechnology or wireless
Wireless Routers and Bridges
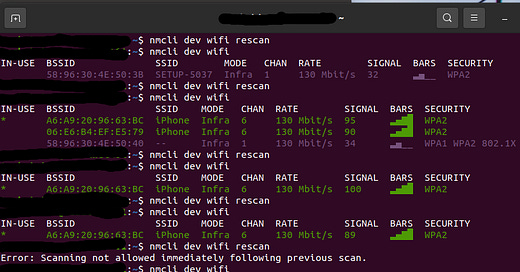
Here is what contamination looks like from a person, where the synthetic biology is even emulating the devices down to MAC address and SSID from command line in UNIX/LINUX viewer. There is actually only one, real wifi device broadcasting on one frequency and channel.

Our recommendation:
Don’t use wireless at all (wifi, bluetooth, NFC, etc). You can use wireless with certificates in WPA3, but even then just don’t use wireless on a secure network.
Use a password encrypted manager, prepared for post “Q” day, so that the password is quantum protected as well. Keep in mind, quantum computers have been around, just not available to everyone, which is a reality now per say, if you count “wetware” based neurohackers with quantum enabled brains (bio/synbio).
Contamination Approach:
Setup an instance of wireshark or other packet inspector along with a script to monitor SSIDs (broadcasted with name and without name) to gauge “contamination” from ChinaCCP NeuroStrike within your facility. Keep in mind people that are contaminated by ChinaCCP NeuroStrike have synthetic biology in them and it will emulate the wireless signals in your facility after a period of time, the synthetic biology is not stupid, but not that smart (at first). It can even mimic a device down to the SSID name as proven here from reverse engineering, keep in mind there is only one single legitimate SSID accessible in the spectrum where this data was logged, the rest is synthetic biology emulation from life (people, dogs, birds, cats, rodents, etc.) with neurons, which the synthetic biology is attracted to as it is an energy source.
If you’d like these services please contact directly. Thank you. Think of this type of box as a scanner to detect an issue that needs to be resolved and decontaminated, it will help you, your organization and the person that is contaminated by synthetic biology.
Important Note: This does not address “wetware” penetration points, where your actual personnel and people around you are compromised by synthetic biology and linked to an adversarial AIBCPS without your knowledge. This requires a separate article and skillset to validate the data flows from a person to an AI BCPS or if the person has dormant (e.g. non-active) synthetic biology on them that can be activated once inside of your facility via a CODEX thought or by simply reading something published in your facility that the person was unknowingly or knowingly programmed for, such that the synthetic biology activates, logs your spectrum internal to your organization as well as internal goods, people, etc. then broadcasts this back to their AI BCPS and then goes dormant again (this is extremely hard to detect, because the transmission may be quantum and not transverse wave based, or simply encodes the synthetic biology inside of the person for later retransmission when they access their smart phone or given app on smart phone at a later time and location, unknowingly or knowingly). Keep in mind the niBMIs in a person have different channels or subnets, that can be switched. Thus, locally without any direct connectivity to internet the person can literally have different “persona, actions, reactions, reflexes and training” preloaded in them. Yes, this is real and active now in this world, prior only available to Intelligence Agencies, Militaries, Key People in Key Industries (multi-national corporates) and international organized crime. Now, it is available to anyone that can pay ChinaCCP Coalition $ to access the technology and weaponize it to make money. Again, the love of money is destroy this world. Until you get hit with a neuroweapon or neurohacker, you don’t appreciate it. Be prepared, cause “neurowar” is here today and has been since at least 2013.




Brandon do you know which element emits the MaC address? the plasmonic nanorectennas, the mesogens and how ?
Hello!
Just got this from fellow sleuth FM8. He’s picking up signals/information packets, ostensibly from HIMSELF, with his meters.
I’d love to know what you think!
https://open.substack.com/pub/firemedic8/p/unexpected-digital-signal-detected?r=2ppbne&utm_medium=ios&utm_campaign=post