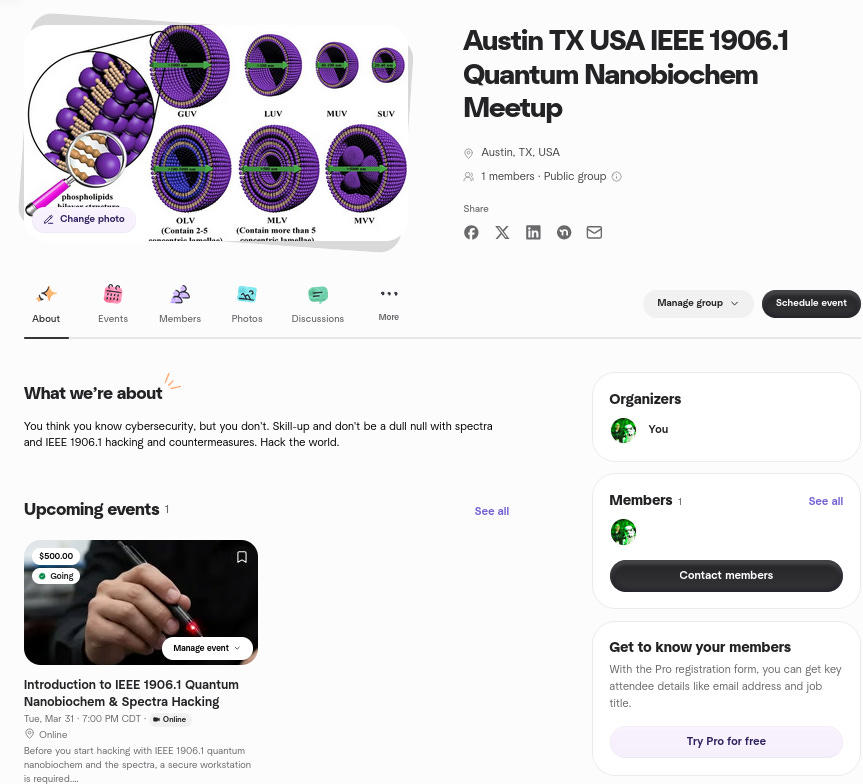
Here is a very useful brief for professionals in cybersecurity that don’t want to get spied on by those in the know with IEEE 1906.1 quantum nanobiochem technologies. There are several levels of protection and this is simply an introductory level applicable for majority of work spaces in a normal work environment. The next level is a SCIF and then a quantum secured SCIF, which is a whole other topic.
I’m doing a meetup in Austin, TX USA and just established a group there for IEEE 1906.1 quantum nanobiochem hacking and countermeasures (red team / blue team) for nanotechnology and spectra hacking and defense in the clear. You can sign-up to the meetup group here. This technology is pervasive and even professional cybersecurity experts are NOT aware it exists. Knowledge is power.
When? March 31, 2026. Where? Is there a cost to this? Yes, this is held-close-to-vest knowledge by the most powerful people on earth in the clear, so yep there is a fee to cover the time spent reverse engineering IEEE 1906.1 quantum nanobiochem.
March 31, 2026 Event at 7 p.m. CST
https://www.meetup.com/austin-tx-usa-ieee-1906-1-quantum-nanobiochem-meetup/
You can also join the meetup group at no fee or cost here to keep tabs on interesting meetups that you may want to attend either virtual or in person.https://www.meetup.com/austin-tx-usa-ieee-1906-1-quantum-nanobiochem-meetup/
The basic secured computer workstation for professionals in cybersecurity against IEEE 1906.1 hackers is able to counter the following data-exfiltration tactics:
EMF (electromagnetic frequencies in the far field that are wireless)
Magnetic Field H-field from the electrical grid
Audio (e.g. sound, longitudinal waves)
Vibrations (e.g. a truck driving by can do this if it shakes the ground enough)
Optogenetic, which is part of EMF, but terahertz and requires polarized glasses and blue-light blockers
Here is how to secure your computer workstation against IEEE 1906.1 quantum nanobiochem hackers. Keep in mind when you get tagged by a quantum nanotech system, it is industrial espionage level technology that was exfiltrated by the intelligence community and military industrial complex that then went into the private corporate world. So, corporations and private groups now have their own version of nation state level IEEE 1906.1 quantum nanobiochem systems, including the big tech firms that totally steal and spy (Microsoft rises to TOP of my list for neurotechnology data theft and brain map theft of Americans and the world, Microsoft for all intents and purposes is on my DROP list as they were also hacked horribly bad by China CCP PLA MSS into their neurotechnology systems and associated security systems). Sorry , Bill, you messed-up when you lost the smart phone battle and then got a hodge podge of security weaknesses installed by default into your computer systems such that it takes a professional cybersecurity person to somewhat harden the insecure Microsoft Windows operating system (cause it’s an open window for IP theft and neurotechnology IEEE 1906.1 quantum nanobiochem hackers).
Have a magnetic salt lamp PEMF H-field at your workstation that can pulse at a sequence that enhances your cognitive ability, such as 40 Hz, 10 Hz etc. (on a random basis) that is NOT on the electrical grid frequency of 60 Hz in America or 50 Hz in Europe. I’ve built prototypes of the magnetic salt lamp and am now moving forward with shipping them with the correct controllers that are NOT internet connected. If you have your smart phone by you it should NOT close to the pulsing magnetic field as intelligence community IC and others can use that magnetometer sensor on it to re-synchronize their monitoring tech. You can go here to inquire www.aibcps.com and scroll down and send an email. These can also be used to sleep at night on your night stand at the schuman resonance frequency.
Have a magnetic repel far-field transmitter. You can go here to inquire www.aibcps.com and scroll down and send an email
Have C60 fullerene contained in shungite in your mitochondria and by you. You can go here and inquire www.aibcps.com and scroll down and send an email
Silver / Nickel faraday apparel on chest and head (e.g. a sweat shirt with a hoodie that has silver and nickel in it). You can go here and inquire www.aibcps.com and scroll down and send an email.
Use of only hardwired internet connect through a VPN such as Nord or Proton that bounces off of many nation states and exist in a state that has “Neurorights” protection so that if anyone is trying to IEEE 1906.1 neurohack, it is illegal. The Neurorights only keeps the good guys honest, not the bad guys and gals.
Use of an internet security appliance such as pfSense that military utilizes. pfSense is an awesome company based out of Austin, TX USA. However, I’ve lost three of their hardware appliances to Electronic Warfare EW attacks and now have over-voltage protection at the computer workstation level and at the building grid connect level (pico-second).
Over-voltage protection via UPS for your computer workstation and the at the electrical grid connect picosecond level over-voltage protection through a manufacturer. I chose to work with EMPshield.com that has picosecond level over-voltage protection for use in Electronic Warfare EW and have it on residence, vehicles and antennas, including satcom. I’ve taken countless EW hits on grid connected infrastructure (having a fluorescent light bulb that is at the edge of going online fully with plasma ionization, but not quite powered up enough is literally the simplest detector for EW attacks, as when your location gets attacked by electronic warfare the fluorescent light bulb will fully energize and turn on resulting in a flicker that coincides with the EW attack for data systems location identification (e.g. the key signal from EW hits a chip in your computer system and that chip phones home to some server for nat-sec or the corporation that made it and their so-called business partners to identify your location and then do a hack into your system).
Electronic Warfare EW Key-signal protection requires both use of a PEMF H-field Magnetic Salt Lamp and Block Box such as MOS equipment. The block box protects against the higher frequency H-field synchronization data exfil attacks, but literally can’t protect against key signals from an ELF based upon laws of physics, so for the lower frequency ELF H-field key-signals the use of a local PEMF H-field Magnetic Salt lamp at your work station is required such that within the 1 to 300 Hz range typical of ELF key-signals the PEMF H-field pulses (set typically below 600 Hz will mess with the actual key signal of the ELF by instead of the key signal only it has the PEMF H-field magnetic pulse in it as well, such that the chipset with a phone home backdoor is not activated due to the summation of the pulses from the ELF key signal + the local PEMF H-field pulser.
You need your computer workstation to be protected against ELF key signal and higher frequency key signal. This requires a magnetic salt lamp and a block box.
You need your cable modem also to be protected against ELF key signal and higher frequency, cause the AI systems will TX frequencies at all your prior known locations. The cable modems all have chipsets with backdoors that phone home and give the IP outlet of your workstation, regardless if you have VPN. Anyone who hacks the chipset of the given cable modem or router can lease space on China CCP PLA MSS world largest psionic ELF and hack that way.
Use of a block box such as MOS equipment’s box here that I utilize
Have an indoor bug zapper in your office to keep the Ns3 DARPA spy bugs away from you (e.g. over-volts them and fries the IEEE 1906.1 quantum nanobiochem) also keep outdoor bug zappers around perimeter to keep the spy bug tech away from you:
Anti-vibration mat or “air bags” under your work station that can be synchronized with the PEMF H-field pulser system driving signal for vibration and magnetic H-field to match.
Windows that are not open with metal shades or faraday curtains.
Polarized yellow glasses with blue blockers on to block the optogenetic programming that typically works in the blue light spectrum through phase-coherence. The polarizing messes with the phase coherence and stops the writes for later recall and review by national security or industrial espionage spies.